Share Azure Blob Files with Active Directory Users using SSO
Azure Blob file sharing with Active Directory users is simplified with NirvaShare. Active Directory is a directory service used by most enterprise organizations for managing users in a centralized manner that govern access across resources. NirvaShare can be easily integrated with Active Directory to enable file sharing of Azure Blob storage with its users. For better file collaboration, AD groups can be used along with fine access control.
Prerequisites
As prerequisites you should:
- Make sure NirvaShare is installed in your environment either manually or from MarketPlace.
To configure the storage, please refer to the documentation below.
Login Profile
A login profile has to be created in NirvaShare to enable SSO with external identity provider. Please refer to below documentation to create one.
Based on the above documentation, please keep the SAML metadata file from NirvaShare ready as the same will be required in further configurations.
Active Directory and Login Profile Configuration
We need to create an application SSO access point, i.e enterprise application in Active Directory to integrate with NirvaShare:
- Sign in to Azure Portal https://portal.azure.com
- Open Active Directory service.
- From the left menu list, click on Enterprise applications.
To know more, you can also visit Microsoft site at HERE.
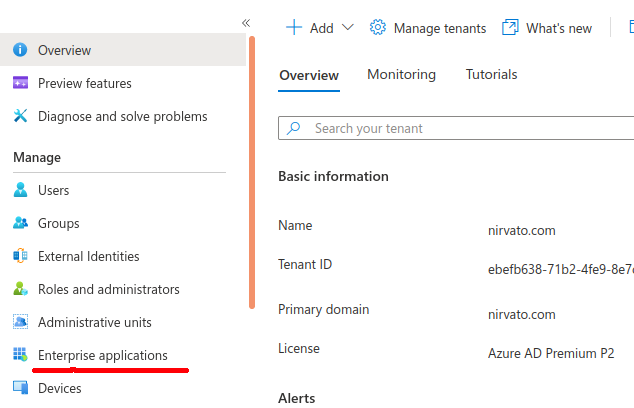
- On the top menu, click on New application.
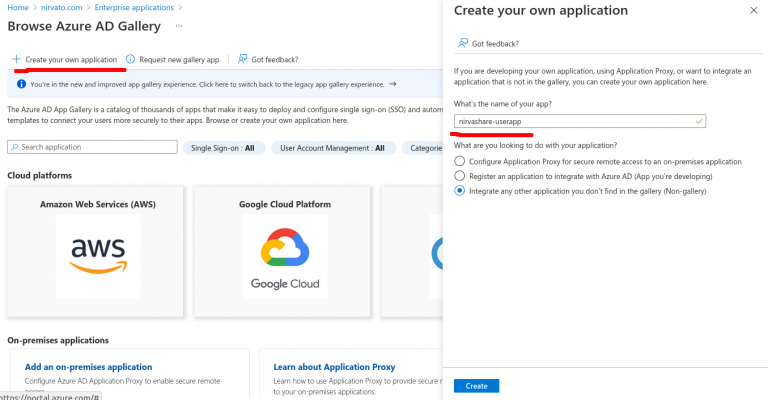
- On the top menu, click on Create your own application.
- Provide a name as NirvaShare-userapp and click on Create.
- Once the newly created application is selected, click on Single sign-on from the left menu tab.
- We need to enable SAML, hence click on SAML block on right hand side.
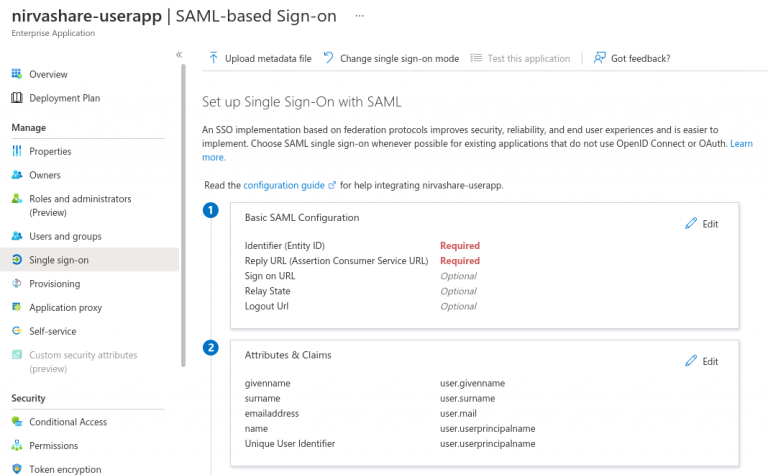
- At this juncture, you will require SAML metadata file that was obtained from NirvaShare based on previous section.
- Click on Upload metadata file.
- Select the NirvaShare SAML metadata file and upload.
- Save it.
- Edit the next section Attributes & Claims.
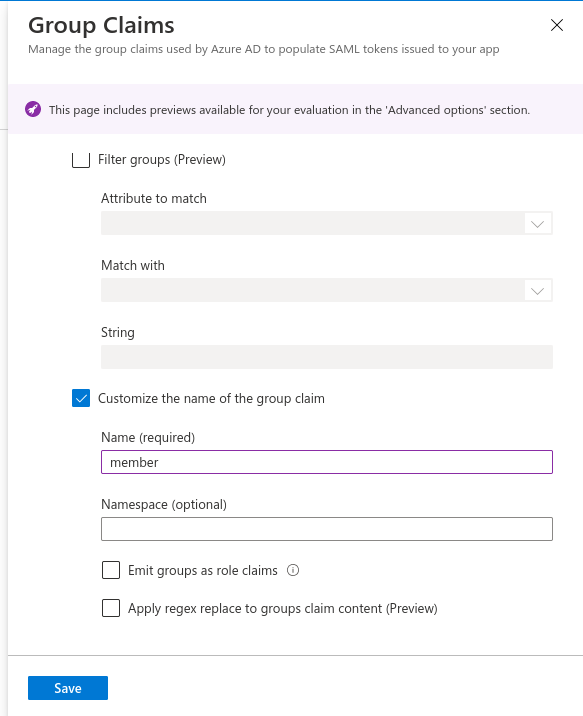
- Click on Add a group claim from the top menu.
- Select All groups radio button and Source attribute as Group ID.
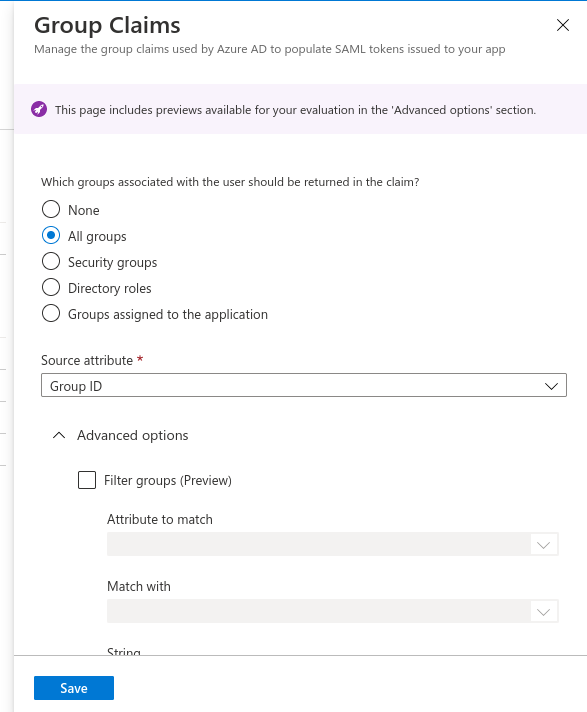
- Scroll down and expand Advanced options.
- Enable checkbox to Customize the name of the group claim.
- Provide name as member.
- Save it.
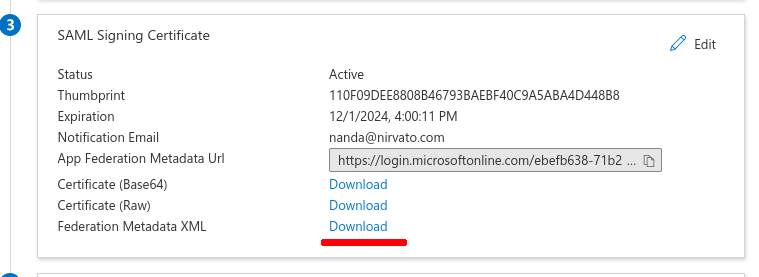
Now, we need to download ActiveDirectory’s SAML metadata file.
- Scroll down to the section SAML Signing Certificate.
- Download the Federation Metadata XML.
- Edit the file and copy the XML content of the downloaded file.
Now let us go back to NirvaShare Admin Console.
- From the NirvaShare Admin Console, edit the Login Profile that we created earlier.
- Paste the Federation Metadata XML content obtained from Active Directory in to the textarea of External IDP SAML metadata.
- Save It.

With this, the required configuration to enable Active Directory Single Sign-On with NirvaShare is done. To test this, proceed with next section to create Shares.
Shares
At this stage, we are good to use the SSO with AD. Let us create a folder Share and enable SSO. Please refer to below documentation to create new Share from the Storage. During the Share configuration, make sure to select the login profile that we created in above section. You can also create one or more shares and assign the same login profile.
Verification
- From the NirvaShare Admin Console, right click on the login profile that we created and select Copy Sharable Link.
- Open the link in browser tab. This will redirect to AD for SSO.
- After the authentication, you will be able to access Shares assigned to the login profile.
