Configure SSO for Admin Console using Google Workspace as Identity Provider
Admin Console of NirvaShare comes with default in-built user store to support multiple admin users. It is also possible to configure Admin Console to use external Identity providers like Google Workspace, Active Directory, etc. In this document, we will configure Admin Console to use Google Workspace as Identity Provider, so that users from Google will be able to login to Admin Console using SAML 2.0.
Prerequisites
As prerequisites you should:
- Make sure NirvaShare is installed either on cloud or on premise. You can also directly install from AWS Marketplace or follow a Manual Installation.
- Configure the Storage and User Application URL. For details check HERE.
- Make sure proper domain name and SSL certificate is configured for Admin Console.
- You will require access to your Google Workspace as console administrator.
Google Workspace Configuration
- Login to Google Workspace admin console https://admin.google.com
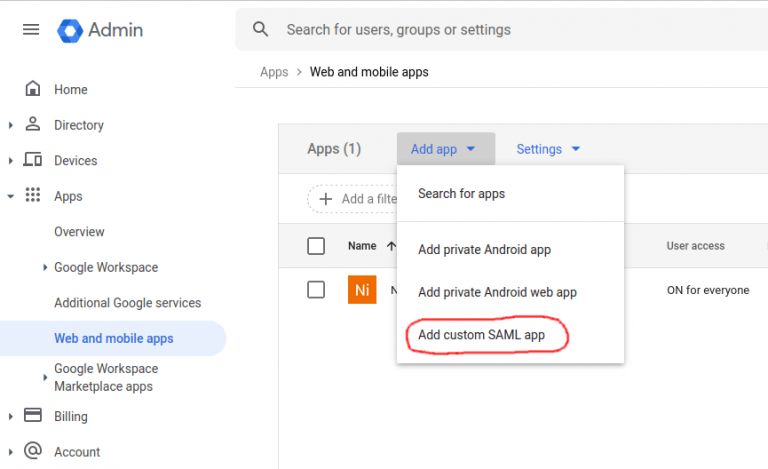
- Click on Apps – >Web and mobile apps from the left menu tab.
- Click on Add custom SAML app
- In app configuration window, for the app name provide a name say NirvaShare-AdminConsole.
- (Optional) For app icon, upload a image for NirvaShare.
- Click on CONTINUE.
- Once again click on CONTINUE.
- This will open the screen for Service provider details.
- For ACS URL enter https://<your domain>/saml/0/acs
- For Entity Id enter https://<your domain>/saml/0/metadata
For Example https://admin.yourcompany.com/saml/0/acs and https://admin.yourcompany.com/saml/0/metadata
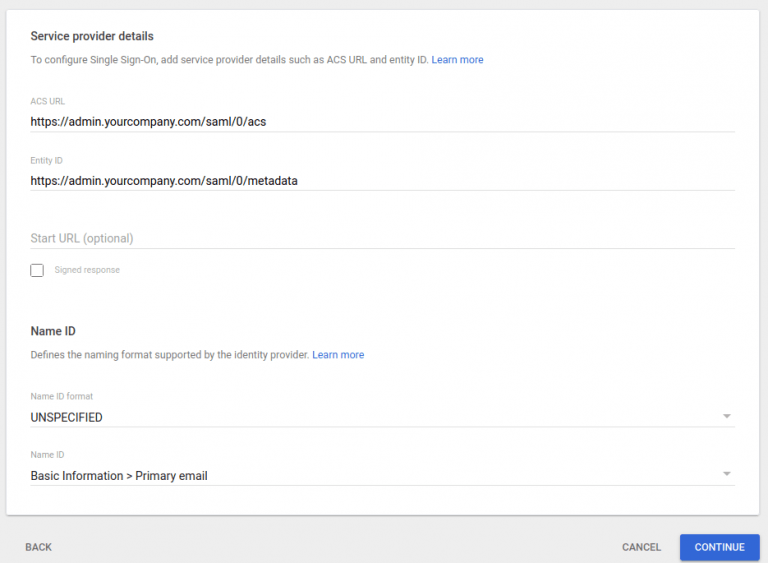
- Click on CONTINUE.
- In the next screen, click on FINISH.
- In User Access page, make sure to give application access to users.
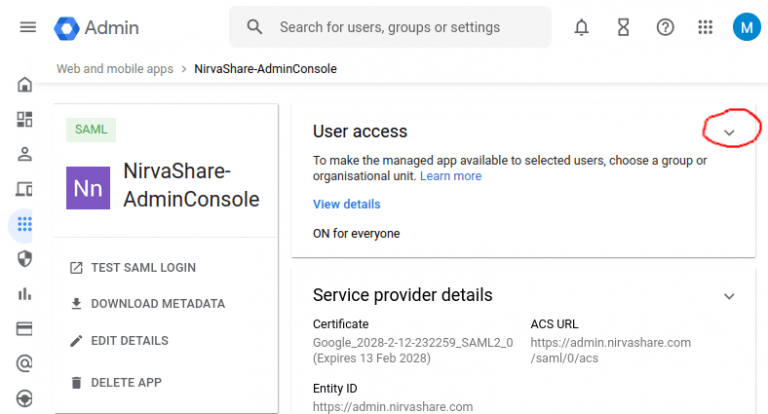
- Select ON for everyone in case if you want to give access to all users from the google workspace account.
- For selective user access, please make use of group or organization unit instead of ON for everyone. In such cases, create a group or organization unit, assign only those users requiring access to the app.
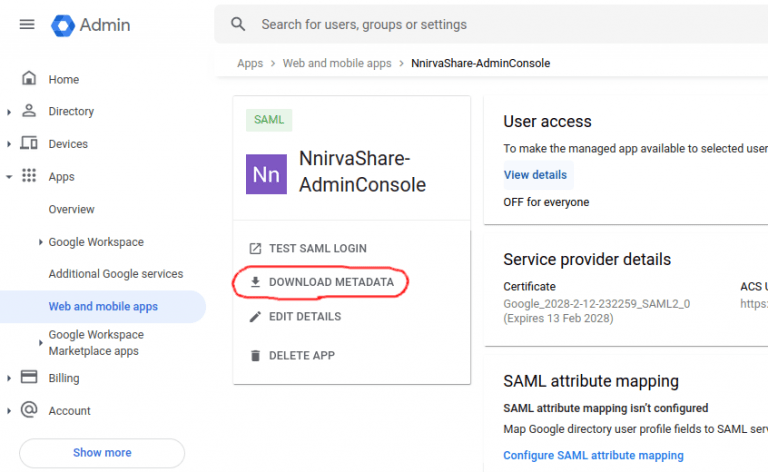
- In User Access page, click on DOWNLOAD METADATA.
- Download and store this metadata file in to your local file system and we will require this file content while configuring the NirvaShare Admin Console.
NirvaShare Configuration
Now that you have the SAML metadata file of Google Workspace identity provider, please refer to the below documentation to configure SSO for AdminConsole of NirvaShare.
After the configuration is done, please open Admin Console https://<your domain name> which will redirect to Google Workspace and perform SSO for authentication.
