Share Files From AWS S3 With Active Directory Users Using SSO
NirvaShare makes it easier to share AWS S3 files with Active directory users. Active directory has become an indispensable part of organizations these days. This is mainly due to its capacity to manage users in a centralized manner and its ability to regulate access control across the organization. To enable sharing of AWS S3 files with active directory users easily and efficiently, one can make use of NirvaShare which is a simple and secure enterprise level file sharing software.
Prerequisites
In order to initiate the sharing of AWS S3 files with Active Directory users using SSO, you should install NirvaShare either manually or from Marketplace.
Storage configuration can be performed using any one of the following two methods
Login Profile
Initially you have to create a login profile in NirvaShare to enable SSO with an external identity provider. Refer the following steps to create one.
In order to create a login profile
- Log in to Admin Console as an administrator.
- Click on Login Profiles from the left menu of the Admin Console.
- Click on CREATE button from the top right corner.
- Provide a name for the title.
- For Authentication, select External Single Sign On (SSO) and click on CREATE.

Note – In order to limit access to only certain white listed IP address or a range, please refer to Access Restriction with IP Address
SAML Metadata
You will require SAML Metadata from the login profile of Nirvashare for the external identity provider integration. Follow the below steps to get SAML Metadata for the newly created login profile to share AWS S3 files.
- Edit the newly created login profile.
- Click on the Download Metadata link.
- This will download the XML metadata file for NirvaShare.
- This metadata file will be required to configure the external identity provider. Hence, please save this file locally for further reference.
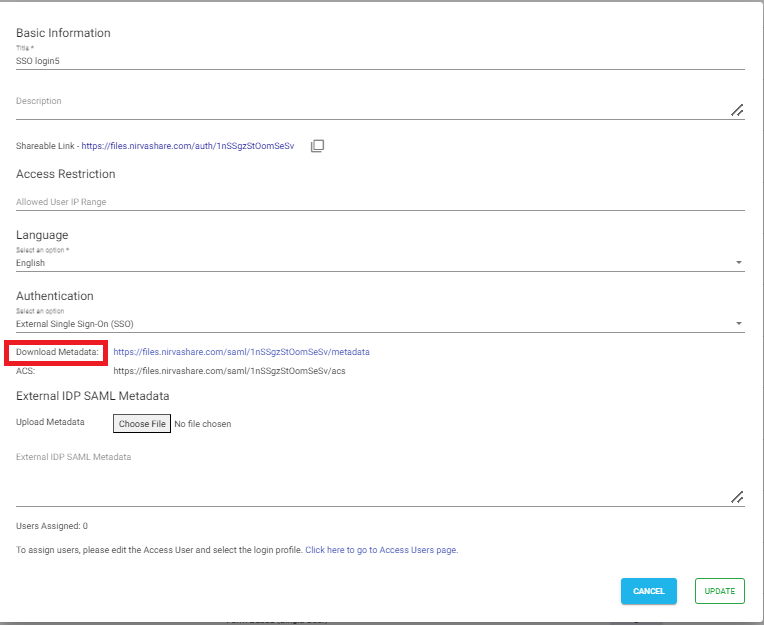
Note – Later stage, you will also require SAML metadata from identity provider and the content of the same has to be provided in the login profile.
Active Directory Configuration
We need to have an application SSO access point, i.e enterprise application in Active Directory to integrate with NirvaShare. In order to get that, we have to make use of the following steps
- Sign in to Azure Portal https://portal.azure.com
- Open Active Directory service.
- From the left menu list, click on Enterprise applications.
To know more, you can also visit Microsoft site HERE.
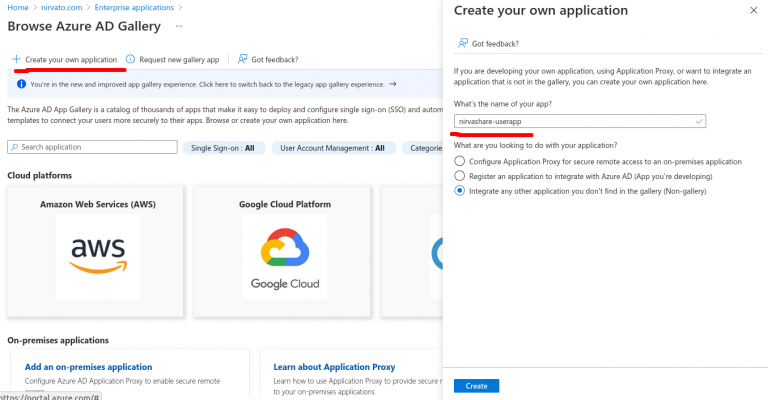
- Go to the top menu and click on New Application
- Click on Create your own application in the next step.
- Provide a name as NirvaShare-userapp and click on Create
- After selecting the newly created application, click on Single sign-on from the left menu tab.
- In order to enable SAML, click on SAML block on the right hand side.
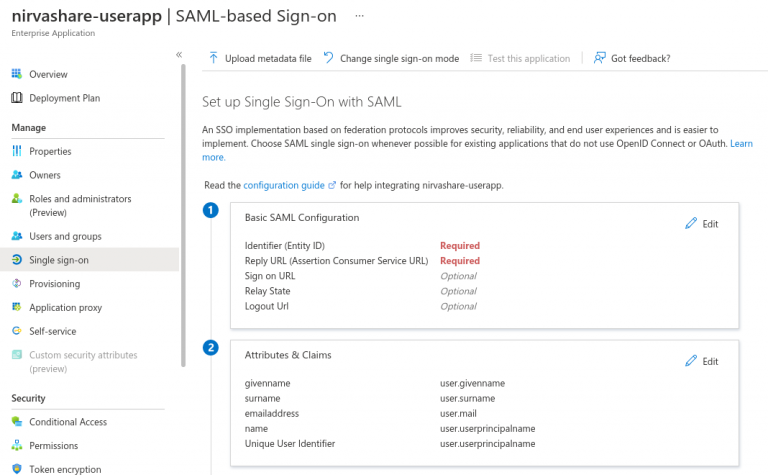
- At this phase, you need the SAML metadata file that was obtained from Nirvashare in the previous section.
- Now click on Upload metadata file
- Select the Nirvashare SAML metadata file and upload.
- Save it.
- Click on Edit in the next section Attributes and Claims.
- Go to the top menu and click on Add a group claim.
- Select All groups radio button and Source attribute as Group ID
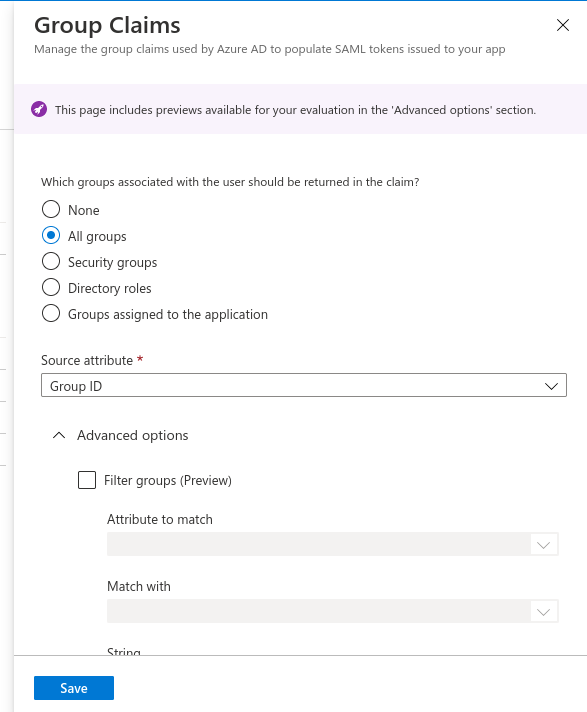
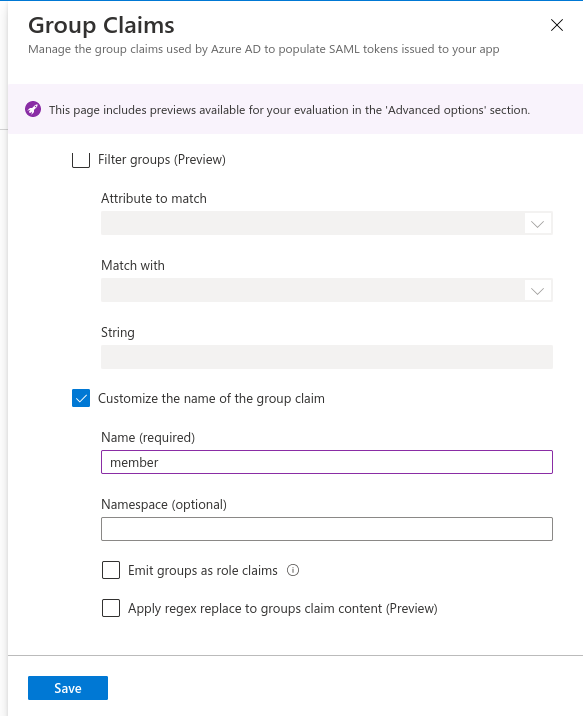
- Scroll down and click on Advanced options to expand it.
- Tick on the checkbox for Customize the name of the group claim
- Enter member in the Name field.
- Click on Save.
In the next step, we need to download Active Directory’s SAML metadata file.
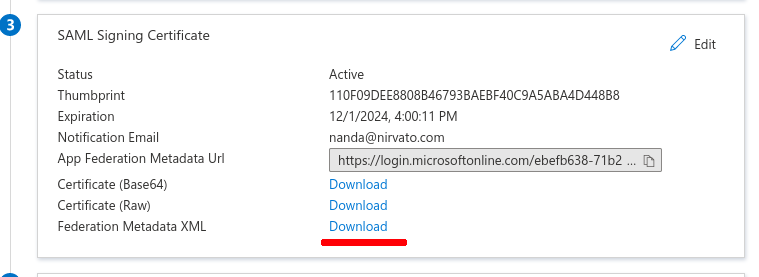
- Scroll down to the section SAML Signing Certificate.
- Download the Federation Metadata XML file.
- Save the file locally.
Updating SAML Metadata
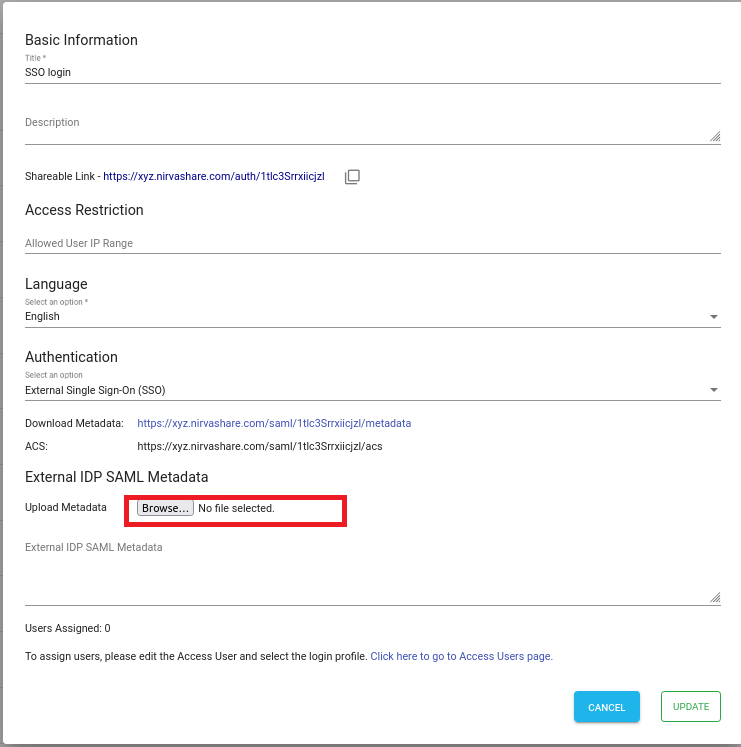
Go back to NirvaShare Admin Console.
- From the NirvaShare Admin Console, click on edit on the Login Profile that we created earlier.
- Upload the Federation Metadata XML content obtained from Active Directory by clicking on Browse next to Upload Metadata under External IDP SAML metadata.
- Save It.
With this step, the essential configuration to enable Active Directory Single Sign-On with Nirvashare is completed. In order to test this, we have to go to the next section where we can create Shares.
Shares
Now we can use SSO with AWS S3. To do this, we have to create a folder Share and enable SSO. Refer to the document below to create new Share from the Storage. While performing a Share, select the login profile you created in the above section. You can assign the same login profile and create multiple shares as well.
Verification
- Go to the NirvaShare Admin Console and right click on the login profile that we created and select Copy Shareable Link.
- Open the link in browser tab. This will redirect to AD for SSO.
- After the authentication, you will be able to access Shares assigned to the login profile.
